Be on the lookout for any suspicious-seeming zoom links or software update SDK “downloads” via Zoom, too. While DPRK state actors are targeting Web3 startups and crypto, it’s still better to exercise caution. Their tactics rely on social engineering for it to work, but the rest is actually a bit complex.
.
 .
.
An Executive Summary by SentinelLabs
- DPRK threat actors are utilizing Nim-compiled binaries and multiple attack chains in a campaign targeting Web3 and Crypto-related businesses.
. - Unusually for macOS malware, the threat actors employ a process injection technique and remote communications via wss, the TLS-encrypted version of the WebSocket protocol.
. - A novel persistence mechanism takes advantage of SIGINT/SIGTERM signal handlers to install persistence when the malware is terminated or the system rebooted.
. - The threat actors deploy AppleScripts widely, both to gain initial access and also later in the attack chain to function as lightweight beacons and backdoors.
. - Bash scripts are used to exfiltrate Keychain credentials, browser data and Telegram user data.
. - SentinelLABS’ analysis highlights novel TTPs and malware artifacts that tie together previously reported components, extending our understanding of the threat actors’ evolving playbook.
.
What to look out for
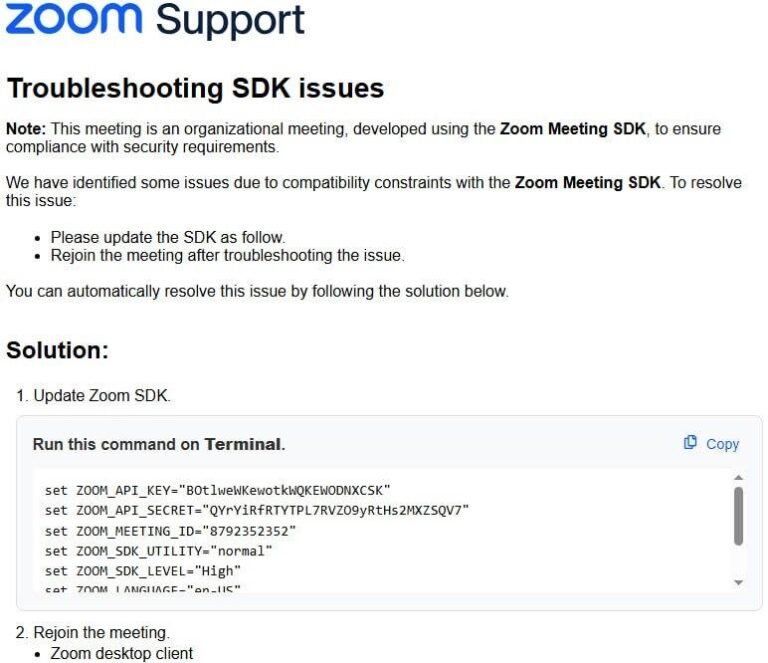
- If someone is asking you to troubleshoot a Zoom meeting SDK on your computer and it feels suspicious, don’t do it. This malware relies on a tactic of social engineering and user input in order to be successful.
. - See: Threat Note: North Korea Calling – Web3 Zoom Campaign by huntability.tech
.
 .
.
Key points of the process
A slightly more detailed “How it works, in a nutshell” was written by Marcus on 9To5Mac explaining it a little more, but these are the key points of the process.
- Someone may approach you on Telegram impersonating a personal contact.
. - You’re asked to schedule a call via Calendly, are sent a follow-up email with a fake zoom link.
. - The Zoom link has a fake Zoom SDK update.
. - Establishes encrypted connection with command and control server.
. - Includes backup logic to reinstall key components if system is rebooted or malware is interrupted.
. - Once it’s all installed, your passwords, keychain, telegram and browser data are scraped.
.
Some notes from SentinelLabs
- “is heavily padded, containing 10,000 lines of whitespace to obfuscate its true function.”
. - “Variants of this script can be found in public malware repositories through the seemingly unintentional typo in a code comment: – – Zook SDK Update instead of – – Zoom SDK Update”
. - support.us05web-zoom[.]forum is the domain name they use. “This domain name format has been chosen for similarity to the legitimate Zoom meeting domain us05web.zoom[.]us.”
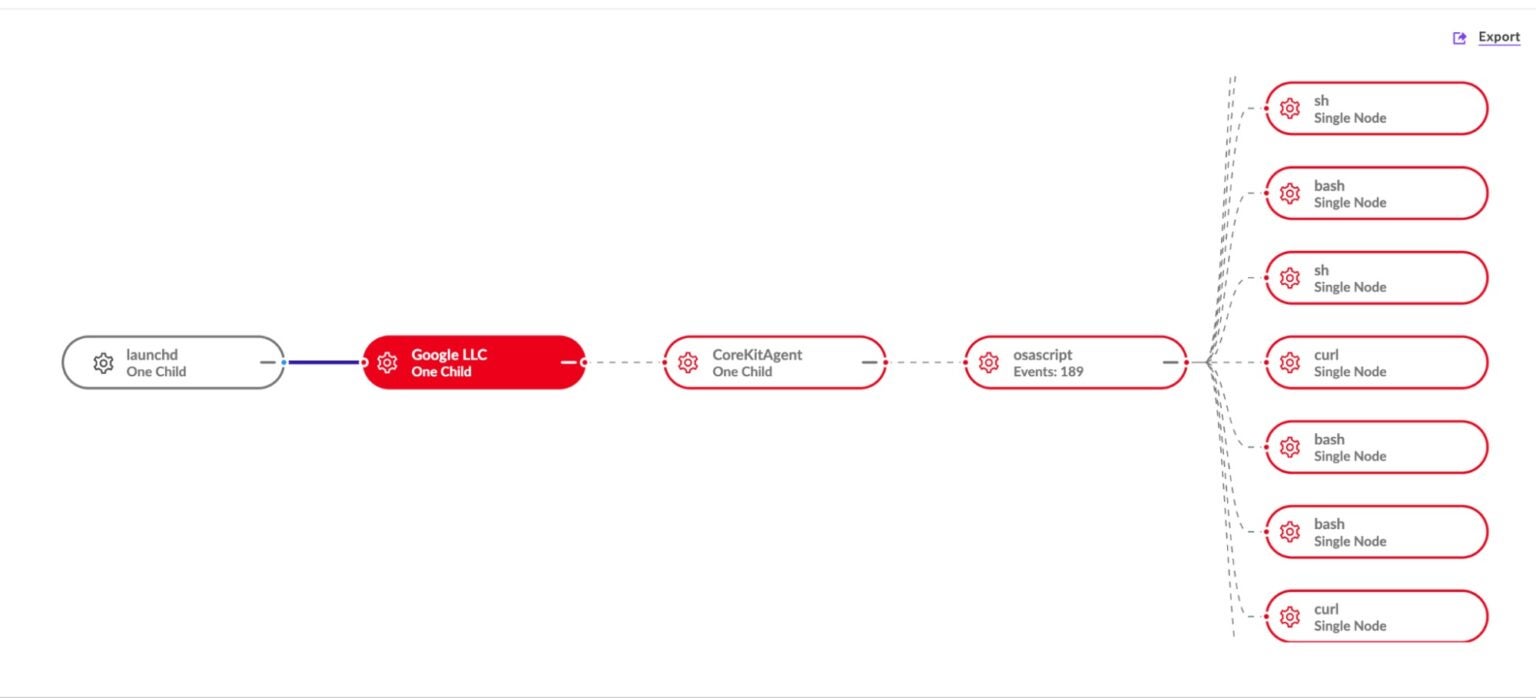 (Above: Execution chain once persistence mechanism is activated. Credit to SentinelLabs)
(Above: Execution chain once persistence mechanism is activated. Credit to SentinelLabs)
My Thoughts
I always think it’s good to point things out regardless, even if the primary attack vector may seem relatively easy to avoid. Attack vectors may change over time especially as their tactics adapt.
It’s worth mentioning how variants of this script can be found in public malware repositories with unintentional typos. It may be possible for someone to unwittingly do this to their Mac, if they don’t pay close attention.

