There’s a new Bluetooth hack out in the wild which could potentially hijack your headphones, potentially track your location, a hack which could wreak havoc if put in the wrong hands. Whether or not you’re an iPhone or Android user, this exploit may affect you depending on which headphones you have. Known as WhisperPair, it affects mostly any pair of headphones which have Google’s Fast Pair, including the latest batch of Beats, which is owned by Apple.

Even if this is a feature you’re not actively using on your headphones, if and only if Google Fast Pair is a feature on your headphones, they are almost certainly vulnerable. This article will discuss the newly discovered vulnerability, how it may affect you, and other bits.
- See the website: WhisperPair – Hijacking Bluetooth Accessories Using Google Fast Pair
. - Malwarebytes: WhisperPair exposes Bluetooth earbuds and headphones to tracking and eavesdropping
. - SecurityWeek: WhisperPair Attack Leaves Millions of Audio Accessories Open to Hijacking
. - See the video: One Tap To Hijack Them All – A Security Analysis of the Google Fast Pair Protocol
What is this about?
To quote the website: “Google Fast Pair enables one-tap pairing and account synchronization across supported Bluetooth accessories. While Fast Pair has been adopted by many popular consumer brands, we discovered that many flagship products have not implemented Fast Pair correctly, introducing a flaw that allows an attacker to hijack devices and track victims using Google’s Find Hub network. We introduce WhisperPair, a family of practical attacks that leverages a flaw in the Fast Pair implementation on flagship audio accessories. Our findings show how a small usability ‘add-on’ can introduce large-scale security and privacy risks for hundreds of millions of users.”

Key notes
- Affects hundreds of millions of headphones by: Jabra, JBM, Logitech, Marshall, Beats, Google, OnePlus, Sony, Soundcore, Xiaomi, and more..
. - How to fix: Phone updates aren’t enough, headphones require firmware updates which is up to the manufacturer. The website has a list of Q&A.
. - When NOT in pairing mode, headphones are supposed to ignore random messages to connect to them. Manufactuers fail to properly enforce this check in their software, allowing unauthorized devices to easily pair.
. - Unfortunately, this attack can easily be done with a single type of script to exploit the vulnerability (i.e; One size fits all). Attacker scans for devices, selects the one they want, and then it’s taken over in a matter of seconds. They force-pair their own device with your headphones.
. - The researchers didn’t publicly disclose about their findings but told Google about it last year, in August 2025. They received a $15K USD “bug bounty” for their discovery.
iPhone users have a specific vulnerability.
- Some headphones support Google’s Find Hub Network.
. - Some iPhone users purchase wireless headphones with this feature + never pair the headphones to an Android device, ever.
. - Non-Android devices such as an iPhone don’t use the Fast Pair feature when connecting to an accessory. However.. the FIRST time headphones with Fast Pair connect to ANY android device in the lifetime of the headphones, they write an account key (which iPhones do not), and will be marked as the owner of the headphones. See in article: What this part means.
. - So if you bought a pair of headphones with Google’s Fast Pair, never paired to an Android device before, then someone else with Android device DOES, that Android device now has an account key associated with those headphones, allowing them to track you.
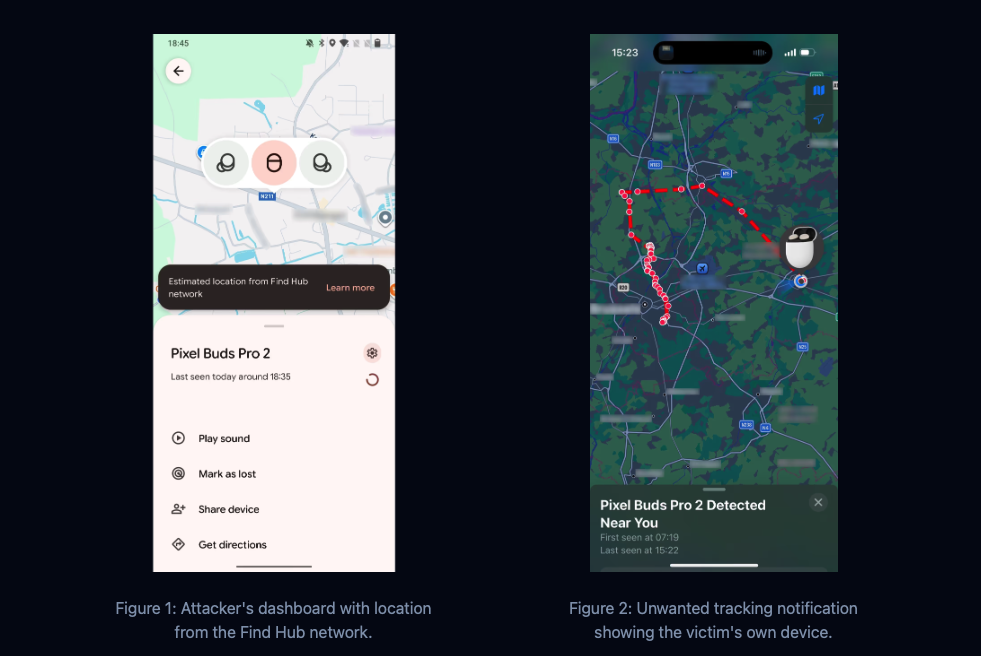 (Source: https://whisperpair.eu/#about)
(Source: https://whisperpair.eu/#about)
- The Victim will see an unwanted tracking notification on their own device which may lead victims to thinking it’s a bug – enabling attackers to track the victim for an extended period of time.

In Conclusion
I believe it’s important to let our readers know of this vulnerability, to stay vigilant and aware. This is indeed a serious issue and was reported as critical by google (CVE-2025-36911), and more information is still yet to be published about this type of attack. In the meantime, it’s best to keep your phone/headphones up to date. Apple’s AirPod lineup is not at all affected in any way shape or form.

