After the Flashback malware made a mockery of Mac security, Eugene Kaspersky said of Apple and Mac OS X, “I think they are ten years behind Microsoft in terms of security.”
And that’s only part of the problem. Dr. Web has analyzed traffic from Flashback compromised Macs and made an interesting discovery: Almnost two-thirds of infected Macs are running a version of OS X 10.6 Snow Leopard. This is despite NetMarketShare reporting that OS X 10.7 Lion and 10.6 currently have the same 2.71% market share. (OS X 10.5 Leopard is way behind at 0.85%, and 10.4 Tiger at 0.20%.)
Here’s Dr. Web’s data for OS X kernel versions that account for at least 1% of infections:
| Kernel version | OS X version | Percentage |
| 9.8.0 | 10.5.8 | 25.0% |
| 10.4.0 | 10.6.4 | 1.68% |
| 10.5.0 | 10.6.5 | 1.23% |
| 10.6.0 | 10.6.6 | 2.62% |
| 10.7.0 | 10.6.7 | 3.58% |
| 10.8.0 | 10.6.8 | 48.41% |
| 11.2.0 | 10.7.2 | 2.47% |
| 11.3.0 | 10.7.3 | 8.05% |
Dr. Web doesn’t report Flashback running under OS X 10.4 Tiger, which is years behind the security curve. OS X 10.7 Lion, which does not ship with Java, has the lowest infection rate at just over 10.5% of the total. One in four compromised Macs is running OS X 10.5 Leopard, leaving us with 64% of infected Macs running OS X 10.6, which is only now being displaced by Lion as the most widely deployed version of OS X.
Apple has updated Java for both Snow Leopard and Lion, several programs have been developed to identify and remove Flashback, and this information has been widely disseminated over the past few weeks.
Why is it that six times as many Snow Leopard Macs are infected as ones running Lion?
Nobody knows for certain, but a leading theory is that because Java is not installed by default, a lot of Lion users don’t have it installed and are thus immune. Another factor may be that Snow Leopard users know version 10.6.8 was the end of the line and may no longer be checking for software updates.
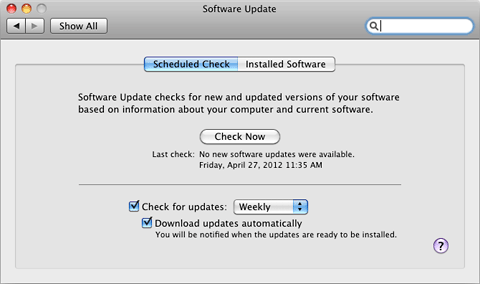
Apple Software Update is a wonderful tool, but a surprising number of users either turn it off or just ignore it. Part of the problem is that Apple simply makes it too easy to disable this useful tool, and part of the problem is that users often don’t know how important getting software updates can be. Apple should consider adding a feature to OS X that pops up a big warning when Software Update has not checked for updates in over 90 days even if users have disabled checking.
Is Apple the Problem?
Like Kaspersky, some are pointing to Apple as the problem. It’s not that Apple makes a lousy operating system, a less secure operating system, or is less concerned with security, but the fact that Apple controls the whole widget. Up to this point, Apple has controlled Java on Macs, and because of that control, Mac users lagged a couple months behind Windows and Linux users in receiving a version of Java that can withstand Flashback. Had Mac users been updated in February, Flashback may have never become so widespread.
Kaspersky recommends that Apple “follow Microsoft’s lead” and let independent software security companies (such as Kaspersky Labs, Symantec, etc.) take the lead against viruses and other malware. Curiously, that’s the exact opposite of Microsoft’s direction. Since releasing Microsoft Security Essentials in 2009, is has become the #1 antivirus program in North America and #2 worldwide. Leading competitors are Symantec, AVG, Avast, McAfee, Avira, and Eset. Oh, and Kaspersky Labs. (Security Industry Market Share Analysis, September 2011)
As Mac users, we may not be aware of antivirus developments in the world of Windows. After all, until a month ago, there was essentially no Mac malware in the wild. On the PC side, antivirus software is a big deal, and in 2011 Avast and McAfee have both increased their share of that market, while Avira and Eset have lost share. It’s a very competitive field with dozens of players.
Apple’s Solution
Apple has kept the iPhone/iPad ecosystem virus free by totally controlling the software market. Apple has to approve any app you can buy for iOS, and one benefit from that is a complete absence of malware. With the Mac App Store, Apple has the same kind of control over part of the Mac market, although Apple has done nothing to prevent OS X 10.7 Lion users from installing non-App Store software.
 When OS X 10.8 Mountain Lion ships in late summer, it will include Gatekeeper, a security system that can protect users by only allowing them to install software from the Mac App Store, from the App Store and “identified developers”, or anything at all.
When OS X 10.8 Mountain Lion ships in late summer, it will include Gatekeeper, a security system that can protect users by only allowing them to install software from the Mac App Store, from the App Store and “identified developers”, or anything at all.
That’s going to provide some additional security, because by default users won’t be able to just download and install software, which is the way a lot of malware infects computers. Gatekeeper won’t let you install them.
I have no idea how that would work with Flashback, since it’s Java code that arrives via your browser, but it should be a great defense against Trojan horses, software presenting itself as one thing (such as antivirus software) while actually compromising your Mac or PC.
Left Behind
There has been a strong antivirus community ever since the VIRUS-L email list was started in 1988, and with the rise of the Internet, malware went from being something spread by floppy disks, the occasional infected CD, and local area networks into something that could go worldwide in short order. Over the past 15 years or so, malware creators have discovered and exploited one security hole after another – and antivirus software developers have risen to the challenge of detecting and removing that malware.
The problem for low-end Mac users is that Apple tends to abandon its older versions of OS X when it’s two versions old. Thus there are no Java updates for OS X 10.5 Leopard now that 10.7 Lion is shipping, and we can expect security updates for 10.6 Snow Leopard will come to an end when 10.8 Mountain Lion arrives later this year.
On my OS X 10.4 Tiger Power Mac G4, the last security update was released in September 2009 (less than a month after 10.6 was released), and the last Java update was June 2009. On my G4 running Leopard, August 2011 for both – a month after 10.7 Lion’s release. And my Mac mini with Snow Leopard had a security update in February 2012 and a Java update in April. After 10.8 arrives in “late summer” (probably August or September), we’ll probably see one last round Snow Leopard Java and security updates and then be left hanging.
Apple is releasing new OS X versions on an annual basis. In the Windows world, antivirus software still supports Windows XP (introduced in late 2001 and under extended support by Microsoft until April 2014), which NetMarketShare reports runs on as many PCs as Windows 7 and Vista combined.
Windows: 10+ years of OS security updates. Macintosh: 2 years.
That’s quite a difference!
The Community Solution
There have been a few projects aimed at keeping old Macs useful in the modern world, most notably TenFourFox (Firefox ported to PowerPC Macs running OS X 10.4 and 10.5), Classilla (an amalgam of older versions of Mozilla compiled to run under Mac OS 9), and iCab (the last version, 4.8, supports OS X 10.3.9 through 10.6.8, version 3.0.5 supports Mac OS 8.5 through 10.5, and 2.9.9 goes back as far as System 7.5.5).
Macs running OS X 10.5 and older have been left behind with Java, and Flash 11 no longer supports the PowerPC platform, so two very useful projects would be compiling up-to-date versions of Java for older versions of OS X (at least back to 10.4 Tiger) and developing ways to run the latest Flash content on PowerPC Macs with OS X 10.4 and newer.
On the malware front, not only have we seen several antivirus companies step into the gap recently, there’s also the open source ClamXav, a free OS X port of Clam AntiVirus (a.k.a. ClamAV) that’s been around for years. Version 2.2.1 is the last version to support OS X 10.4, and virus definitions are still being updated for it. ClamXav 2.2.5 is the current version, and it requires OS X 10.5 and newer.
We are very fortunate that thus far Flashback has not been compiled for PowerPC Macs, nor does it seem to run under OS X 10.4, but that doesn’t mean it can’t or won’t be done – or that some future malware won’t attack that increasingly small segment of the Mac market.
With Apple now abandoning versions of OS X after just two years, it’s time for Mac users and developers to team up if we want to keep our low-end Macs secure and relatively up-to-date. Kudos to those already doing so – they are paving the way for others to follow the path they’ve blazed.
Keywords: #flashbacktrojan #osxsecurity #macsecurity
Short link: http://goo.gl/QfTEih
searchword: macinsecurity